14-Jan-2025
THX Trademark as a sound– this. [fair use requested] a certification system for movie theaters
that is:
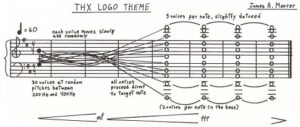
Someone called Jess Durbin multitracked himself to sound like this!
Lineage OS for you older Android tablet or phone that won’t otherwise update
Kevin McCloud the composer that you have often heard, but never heard of
the honey/paypal scam: Google it!
Use your phone in older car? a $70 7″ Display can help if it uses apple “CarPlay” or “Android Auto”
so it looks like a way newer car! Amazon example only
Some Audio & Video A.I. tools whatver you think of them- there are A LOT
AI Video Editor and Audio Cleanup and Video Cleanup and FireCut and OpusClip
31-Dec-2024
Last show and 5th Tuesday of the month- New Year’s Eve was Substituted with Non Zen Tech
24-Dec-2024
Christmas Eve! Pre recorded not all Tech show– some Music!
12-Dec-2024

Ideas for the holiday season:Framed photo prints Ex:https://frameology.com
|or better yet a Photo Frame
Woodstoves. Ah, Wood-stoves! A bit about Creosote, flues,moisture… Baffle Boards,etc
The best way to do charitable giving: Never at the Door, Never on Facebook,
never on impulse
Check the Credentials IN YOUR OWN TIME- Commissioned Reps should give you an affiliate ID. NonProf? Not all are as they seem to be.
“Give in Kind”- Car, goods, etc. Consider Give Local.
Why dishwasher drain hoses have a non-return valve?
And if they do not, do you need an air gap?
Android/iPhone text messaging vulnerability due to Chinese hacking of RCS
(rich communication service)
Spam phone calls, and “verified. Sender status”. VSS
Google Gemini app now available for playing with AI
Also: voice-faking: Have a “Safe Word(!)” or ask something only the “real” caller could know
“Generative AI Voice Cloning” See Here
Sites using AI Voice and Text as Sales Tools- Just Use It Yourself.
App/play store: watch out for sponsored apps, and look alike apps with their names and icons

26-Nov-2024
Happy Upcoming Thanksgiving!
Glen is in Madrid in the Wee Hrs so may not be able to call in : )
– New thumb print locks for Not Much Money
– ESP32 Thermostats and Zigbee/BlueTooth Gateway!
– Bombarded by Scam Spam Scum on your iPhone?
Consider re routing through Google Voice/TAlk account
Blocking is Useless.
– Data Brokerage and what it means to you_
– Music.YOuTube.Com and Novelty songs….
– Software Companies ar now designing Hardware Chips- and using AI to Do it.
What happens when stuff now knows how to make itself? (Gray Goo Theory)
– Alternatives to Adobe.. Ill get a better image eventually!

